What is PCI again?
The full name (PCI DSS) stands for Payment Card Industry Data Security Standard and it’s a set of rules to help keep cardholder’s information secure. In the past, I’ve written about how to achieve and maintain PCI compliance. For a quick refresher, PCI refers to security standards that apply to all businesses that accept credit cards. Technically, the standard refers to “storing, processing, or transmitting” card data, but if you accept cards, you’re doing one or more of those things. Achieving (and maintaining!) PCI compliance is critical, as it reduces your risk of data breaches (and can help limit your liability in the event of a breach) and helps minimize avoidable fees from your credit card processor. The most common one is the PCI non-compliance fee, which processors will charge each month that you aren’t PCI compliant. But PCI standards have gotten an update to PCI DSS 4.0 and that is what you’ll now need to comply with.PCI 4.0 Timeline
PCI version 4.0 was released in March of 2022, but the prior standard was intentionally left in place for 2 years following its release to allow time for assessors and businesses to understand the changes and make updates. Additionally, some requirements were “future-dated” meaning they wouldn’t be required until a specific date. All requirements went into effect in March of 2025, so the standard is now considered fully implemented.What changed in PCI 4.0?
It comes with many changes from the prior version. Some may not apply to your business, but we’ll include them here for reference. The PCI DSS website includes an infographic about version 4.0, stating these goals: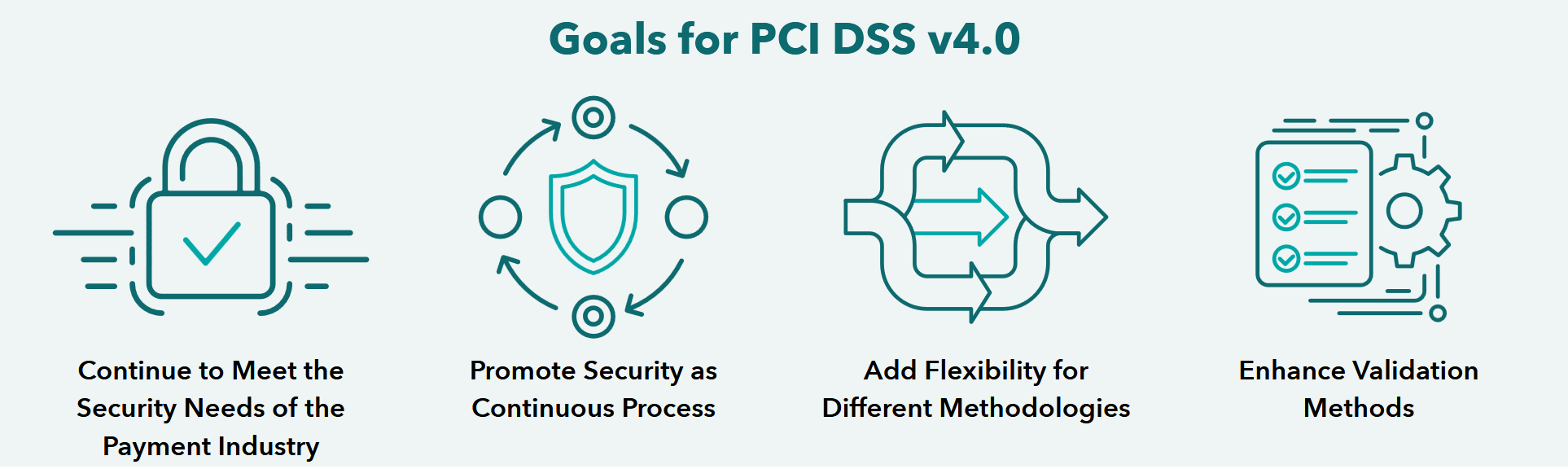 Let’s take a look at what specifically changed.
Let’s take a look at what specifically changed.
Approaches to Meet Requirements
In the past, the only approach for meeting PCI was a checklist, now referred to as the “Defined Approach.” You may recognize the Self-Assessment Questionnaire (SAQ) that businesses using the Defined Approach will submit. That option is still available and will be useful for most small businesses. The change is the addition of the “Customized Approach,” targeted toward larger businesses that have in-house cybersecurity teams. With the Customized Approach, a business’s in-house team can analyze the requirements and the intent behind them, implement equivalent (or better) security, and provide their own documentation with an assessor to prove effectiveness. This is geared toward larger businesses with their own unique infrastructure, hybrid cloud environments, or alternative security solutions. However, this approach must prove that the implemented solutions are as effective (or more effective) than what is spelled out in the standard.Defined vs. Customized Example
For example, one requirement is a password minimum length of 12 characters. In the Defined Approach, the business would need to ensure that passwords are set to require a minimum of 12 characters. In the Customized Approach, the cybersecurity team can review the requirement, determine that it is about secure passwords, and decide that their implementation is stronger. That team may decide to use a fingerprint login with multi-factor authentication and then test it with a qualified security assessor to confirm it provides equal (or better) security than the 12-character minimum password requirement. Here is a quick look at the differences between the Defined Approach and Customized Approach.| Defined Approach | Customized Approach | |
| Compliance Method | Meeting specific, pre-defined requirements | Customizing security controls to meet the goals of the standard |
| Flexibility | Low (business must adhere to exact requirements) | High (business can create methods that achieve the same goal) |
| Documentation | Checklist. Fill out a self-assessment questionnaire (SAQ) | Provide detailed documentation & risk analysis from your internal team and independent assessor |
| Testing | No additional testing required beyond SAQ | Must undergo testing and QSA review for custom controls |
| Security Objective | Based on defined security requirements | Based on risk assessment and security goals of the organization |
| Best for | Small to medium businesses or businesses with non-custom setups | Large businesses, those with in-house security teams, and businesses with complex or custom IT infrastructures |
A Note on the Defined Approach
The Defined Approach does have an option for businesses with a constraint that prevents them from meeting the requirement as stated. Called “Compensating Controls,” this option allows a business with a “legitimate and documented technical or business constraint” that prevents them from meeting a requirement to implement other controls that mitigate the risk. Compensating Controls are different than the controls implemented in the Customized Approach. With that in mind, let’s take a look at the specifics of the Defined Approach.Stronger Password Rules
The example above is a real new requirement for the Defined Approach. If you have an existing password policy at your company, you should update it to account for these new rules:- Passwords must be a minimum of 12 characters (up from 7 previously)
- Passwords cannot be reused
- Passwords should not be easy to guess
Required Multi-Factor Authentication (MFA)
Version 4.0 of the PCI standard now requires multi-factor authentication (MFA) for any access to cardholder data. Previously, this only applied to accessing cardholder data remotely, such as for an employee working from home and accessing your systems. Now, employees logging in from your store, office, or restaurant (in addition to anyone logging in remotely) must use secondary verification, such as a code sent to their phone or email, to verify the login.Regular Risk Reviews
In the past, you only needed to perform risk reviews as part of an annual review. Now, you’ll need to review and document security risks more regularly. This is part of the 4.0 standard’s push for more proactive security that keeps pace with the changing nature of security risks and fraud. Technically speaking, the standard doesn’t have a strict requirement for how often the reviews must be conducted, but it does strongly suggest at least quarterly risk assessments where you review any potential risks to your payment processing system (including cardholder data) and your IT infrastructure. You’ll need to identify any new vulnerabilities, including those that could be discovered in your processing software or hardware. To do this, you should be sure to stay current on fraud updates or security patches available from your POS system and credit card processor. You’ll need to document your reviews, including any identified risks and what changes you’ve made (if any) to address those risks. You can also choose to do risk reviews when potentially-impactful events happen. This includes hiring new staff, updating your POS system software, or learning of a data breach for a similar business.Assigned Roles
To drive accountability, you’ll need to assign a designated person or role to each PCI requirement. Even if the requirements are assigned to the same person or the same few people, you’ll need to document it in order to formalize the accountability for that requirement. Typically, most small business owners will assign themselves unless they have in-house IT or cybersecurity staff, in which case that person may be assigned. If you’re assigning responsibility to one of your employees, be sure to talk through the requirements with them and make sure they understand what they are accountable for.Encryption and Access Control
While data security has always been part of PCI, the 4.0 version requires transport layer security (TLS) 1.2 or higher to protect cardholder data during transmission through encryption. It replaces older protocols such as secure sockets layer (SSL) and TLS before version 1.2. TLS deals with transmission between systems, such as your credit card machine and your credit card processor. You can work with your processor to ensure the latest security tools are used. This is one of the future-dated requirements when the standard was released in 2022, but is fully in effect as of March 2025. In addition to encryption during transit, the standard requires stronger protection for data “at rest” or data that is stored. Cardholder data (which includes account numbers, expiration dates, and CVV codes) stored in any system must be strongly encrypted. Businesses that store data should be using secure storage vaults from credit card processors or third parties, which will help mitigate the risk of unencrypted at rest data.Access Control to Encryption Keys
Access to encryption keys (the method for encrypting and decrypting data) must be restricted to authorized staff only. Additionally, encryption keys should be rotated periodically and properly destroyed when not in use. Your credit card processor or card storage vault company can provide more information on encryption practices.Access Control to Data
In addition to access to encryption keys, access to sensitive data (such as cardholder information) should be restricted to only authorized personnel. To help ensure that, the standard recommends role-based access control to restrict access based on an employee’s role. Employees without a business need to access sensitive data will not be able to do so. Additionally, as already noted, any employees accessing cardholder data must use multi-factor authentication.How do I do all these things?
For many small businesses, PCI compliance seems like a daunting task. However, if you break it down into smaller chunks and utilize support available to you, such as your credit card processor, it can be easier than it sounds. Here are some things you can do right now, if you haven’t already:- Enable multi-factor authentication on all your systems
- Update your password policy and work with IT to ensure that password requirements are met
- Document who is responsible for which aspects of security at your business
- Do a security risk assessment with your IT person and / or credit card processor to make sure you’re not breaching any requirements
- Complete the self-assessment questionnaire, or talk to your processor about assistance
- Encrypting cardholder data during transmission
- Encrypting cardholder data “at rest” if you utilize a secure card storage vault your processor provides
- Managing encryption keys
- Releasing software “patches” for security risks or vulnerabilities (but you’re still responsible for updating your software to the latest versions)