If you’re dealing with credit card payment information, sensitive financial data, or other details relating to money and finances, you need to ensure your data is safe.
With the increase in scammers and hacking, staying on top of information security is vital. Coalfire is a cybersecurity business that provides a variety of cyber security, auditing, testing, scanning, and other services.
In this review, we’ll explore what those services are and how they can help you keep client data safe.
About Coalfire
Coalfire is a security technology and consultancy business, started in 2001. It focuses mainly on risk management, reducing cyber threats, and helping businesses comply with various security-related rules and regulations. Its compliance work includes mandates issued by governments, industry bodies, and others.
On the technical side, it also provides advice on security best practice and IT infrastructure, aimed at reducing the risk and severity of information breaches. The company is a member of numerous security industry bodies and has many accreditations from technology providers, agencies, and other areas. Its clients include household names like 3M, AXA, Amazon, GoDaddy, IBM, Intel, Intuit, Oracle, NCR, Shopify, Toshiba, and more.
The company’s mission is “to provide knowledge, tools, guidance, and independent assessment services to all organizations.”
PCI DSS Audit and Assessment
One of the most important areas for credit card processors and businesses that accept credit cards is being compliant with the Payment Card Industry Data Security Standards (PCI DSS). Coalfire provides a complete range of assessment services designed to audit and understand a company’s PCI DSS implementation.
Their services cover all areas of PCI DSS including policies, procedures, security management, technology, infrastructure, architecture, software, design, protective measures, and more. They can tailor their services to a payment provider’s auditing and reporting needs, whether that’s a self-assessment questionnaire, or a complete report. Their consultants are Qualified Security Assessors (QSAs).
Services provided include:
- Facilitated self-assessment
- PCI DSS scope definition, advice, and recommendations
- Audits of point-to-point encryption and other systems
- Compliance reporting
Related Article: Understanding PCI Compliance.
PCI DSS Scans
Many businesses will need to complete external, independent PCI DSS scans. Coalfire can provide this service. They can scan your PCI DSS implementation on a monthly, quarterly, or annual basis and provide a complete report that can be shared with your credit card networks and other necessary parties.
PA-DSS Validation
Coalfire can protect from identity theft, credit card data theft, and other problems through Payment Application Data Security Standard (PA-DSS) validation. Coalfire will:
- Complete a company risk assessment
- Review and verify security protocols and processes in card reader hardware and software
- Audit payment processing solutions to ensure they comply with PA-DSS requirements
- Evaluate the software or hardware’s handling of payment card data
- Validate and confirm segmentation controls
Digital Forensics
In the event of a breach, Coalfire has dedicated digital forensics experts who can examine the issue and provide evidence, information, and preventative measures. These services include:
- Breach analysis — Exploring information around the incident, including timelines, compromised areas, malware, vulnerabilities, interdependencies, and affected data.
- Device investigations — Research of mobile device usage that could contribute to a breach including forensic analysis, keyword and pattern searches, and credit card data.
- Scanning and prevention — Evaluating every part of your data security systems to identify malware, weaknesses, or other exposure, then providing recommendations to close gaps.
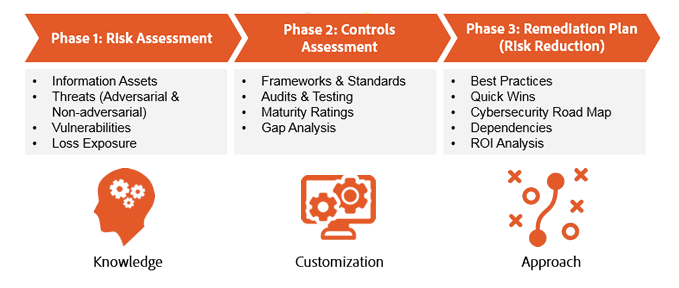
Vulnerability Scanning
It’s important to secure your network against hackers, malware, and other malicious actors. Coalfire provides a vulnerability scanning and assessment service. Key features include:
- Automated scanning of every part of your infrastructure to identify breaches
- Network vulnerability assessments through manual validation and analysis
- Detailed risk analysis together with a complete report on vulnerabilities and other issues
- Recommendations to remove points of failure, strengthen security, and prevent unauthorized access
Penetration Testing
Penetration testing (often called pen testing) is designed to test the security of your systems by carrying out simulated “attacks” in a similar way to how a hacker would go about accessing sensitive information. It can help businesses find and patch critical vulnerabilities before they can be exploited by real-world criminals. Services include:
- Brute force attacks to find weaknesses in your security systems
- Internal and external penetration testing and threat assessment
- Targeted attacks at known vulnerabilities to check all parts of your infrastructure have been properly patched and maintained
- Social engineering testing to see if your employees could make your data vulnerable
Application Validation and Security Testing
If your financial organization uses online applications to interact with customers and transfer financial data, it’s important to ensure those applications are secure. Coalfire will conduct security testing to identify any weak spots and provide recommendations to keep customer financial information secure. The company scans for application vulnerabilities and design flaws, manually reviews weak areas, and provides recommendations to close gaps and ensure security.
Social Engineering Testing
Social engineering is a process hackers and other scammers use to get access to sensitive information. It involves gaining the trust of employees or other stakeholders and influencing them to provide sensitive information including network access, passwords, and other compromising details. Coalfire carries out social engineering testing in several areas:
Email Phishing
Email users can be tricked into clicking on links that reveal personal information, passwords, and other sensitive data. Coalfire carries out phishing assessments to understand employee IT security awareness.
Pretexting
Employees can be influenced through the use of “pretext” (e.g. someone claiming to be from IT calling an employee and requesting a password.) Coalfire’s security assessments determine if employees are likely to be fooled by this approach.
Physical Environment
Some criminals will try to physically access your office. Coalfire’s assessment checks your access policies and procedures to see if that could happen to your organization.
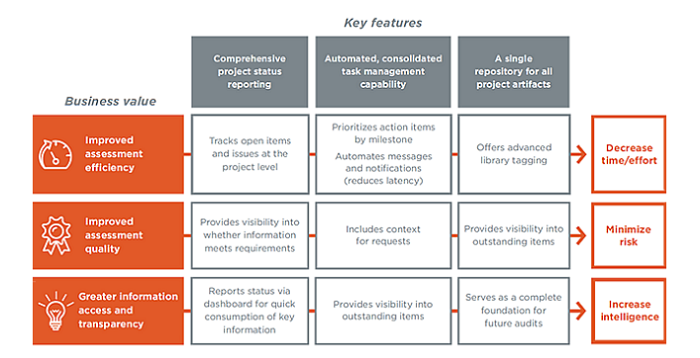
Coalfire One
Coalfire One is Coalfire’s security suite. It provides a portal where clients can access various automated security programs to ensure their businesses remain safe and compliant. Services provided by Coalfire One include:
- Automated vulnerability scanning of external and internal networks.
- Information to assist you in completing financial compliance and assessment processes.
- PCI DSS self-assessment tools and questionnaires.
- Project management tools to ensure security and encryption is embedded in project management methodology and delivery.
- Document management and reporting tools.
- Access to professional support and expert security consultancy services.
Coalfire One Scanning
The Coalfire One scanning application provides several services:
- Scans and alerts you to potential vulnerabilities and issues.
- Searches networks, applications, and other areas for common attack vectors and known security issues.
- Identified potential breaches that could expose financial, credit card, personal, and other sensitive information.
- Scans for both known malware and malware signatures.
- Allows for compliance with industry-specific mandates.
Coalfire provides a range of security services that are well suited to credit card businesses, payment processors, and other financial services providers. If you want to stay compliant, protect your business from vulnerability, and identify any issues, their services can help you secure sensitive data and information.



